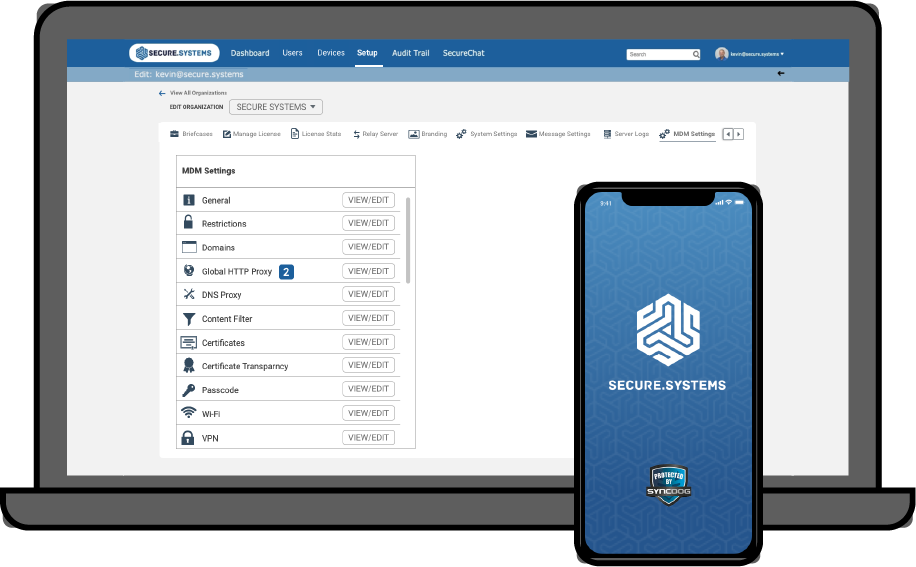
Mobile Device Management (MDM)
The Industry’s first fully integrated Mobile Device Management solution.
Remote Management
Policy Configuration
Device Control
Device Configuration
Complete End-to-End Mobile Security Platform
Today, it’s very important for enterprises to manage devices used by team members on the organization’s network to ensure the success of identity and access management as well as optimization of functionality and device security.
Secure.Systems is a comprehensive mobile device management solution designed to empower your mobile workforce with the power of mobility, by enhancing employee productivity without compromising on corporate security.
With SyncDog we include device tracking, inventory, application distribution, password verification, and enforcement, as well as data encryption.
Device Management
Single console for complete mobile device management
App Management
Track the entire lifecycle of apps
Security Management
Enforce security policies
Email Management
Configure, secure, and manage corporate email
Content Management
Securely share, save and view documents on devices
Containerization
Separate personal and corporate data
360° integrated support for secure mobility
Quickly bring devices under management
Easy enrollment and authentication for BYOD and corporate devices.
Intuitive dashboard with an easy to use interface
Management has never been simpler with an overview of the entire device ecosystem in your organization.
Ensure devices are compliant with policies
Configures profiles to enact policies for Wi-Fi, VPN and other parameters.
Mobile Device Management Features

Device Enrollment
Enroll devices manually, in bulk or make users’ self-enroll their iOS or Android devices with two factor authentication.

App Management
Install in-house and store apps seamlessly, build your own app catalog, restrict blacklisted apps and more.

Profile Management
Create and customize policies and profiles for different departments/users and associate them with a variety of groups.

Email Management
Manage and secure corporate emails through Platform Containerization and Exchange ActiveSync.
Kiosk Mode
Restrict your device to access a single or a specific set of apps.

Remote Troubleshooting
Remotely view and control mobile devices. Solve issues related to devices in real time.

Asset Management
Fetch the details of installed apps, enforced restrictions, installed certificates and device hardware information.

Security Management
Customize intricate security policies such as the passcode, device lock to protect corporate data from outside threats.

Content Management
Remotely share content to the devices. Securely save and view documents on the devices.
Audit and Reports
Audit mobile devices with pre-built reports such as Rooted Devices, Devices with Blacklist Apps, etc.

Rugged Device Management
Complete lifecycle management of ruggedized laptops and handhelds.
Integrations
Manage devices from a unified console by integrating with other business essential applications.
SyncDog is your seamless mobile security provider
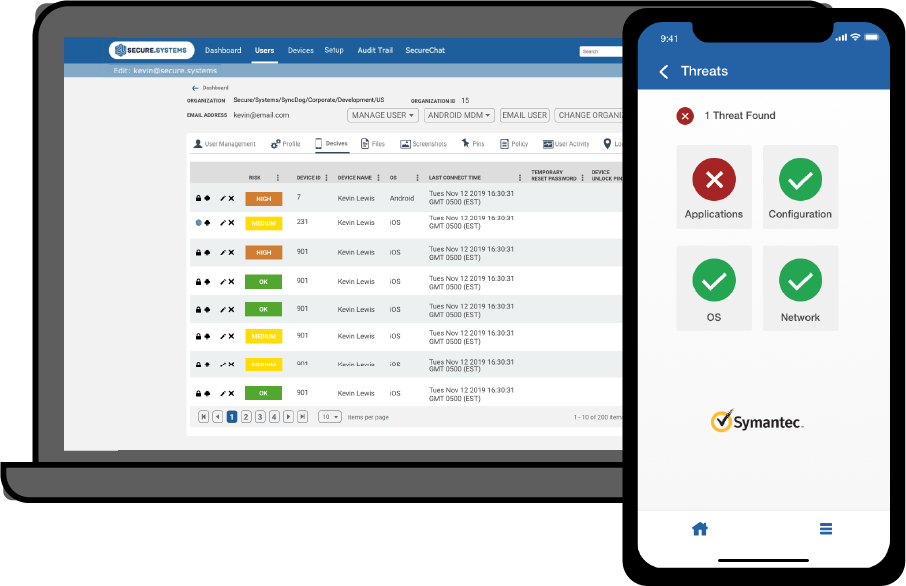
Mobile Threat Defense
SyncDog offers an end-to-end solution for mobile enablement and security, keeping mobile workforces secure without inhibiting productivity outside of the office.
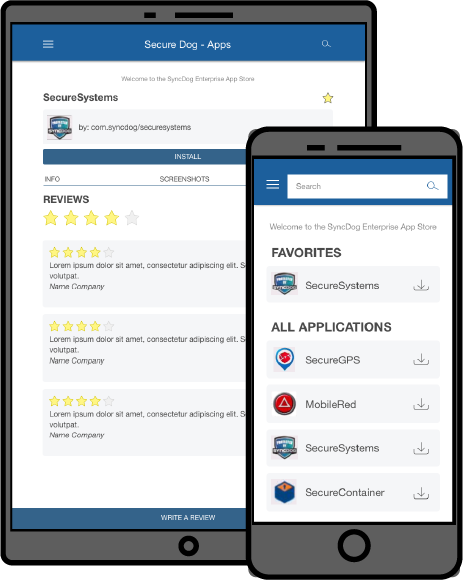
Private App Store
SyncDog is a leading provider in Mobile Application Management (MAM) for enterprises. From government to healthcare, we provide complete management of mobile apps delivered securely in the Cloud, on site or a hybrid solution.
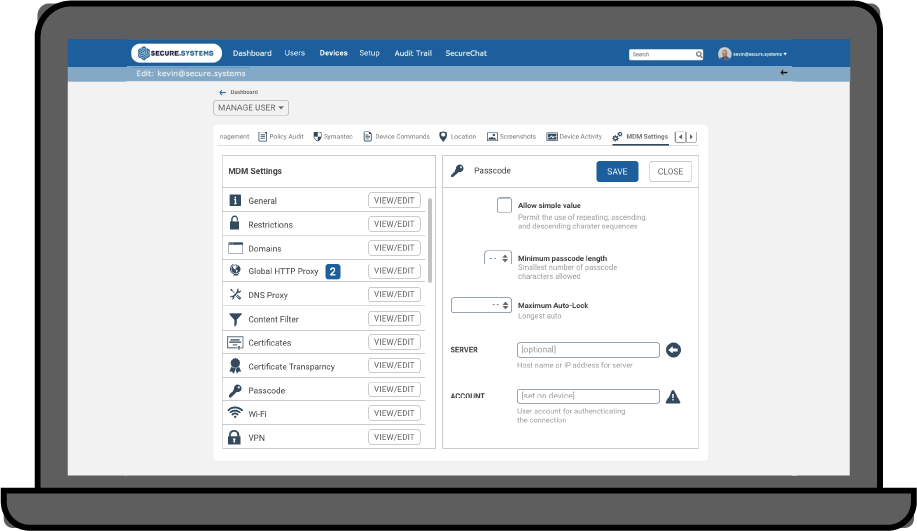
Containerization
SyncDog is a leading provider in Mobile Application Management (MAM) for enterprises. From government to healthcare, we provide complete management of mobile apps delivered securely in the Cloud, on site or a hybrid solution.
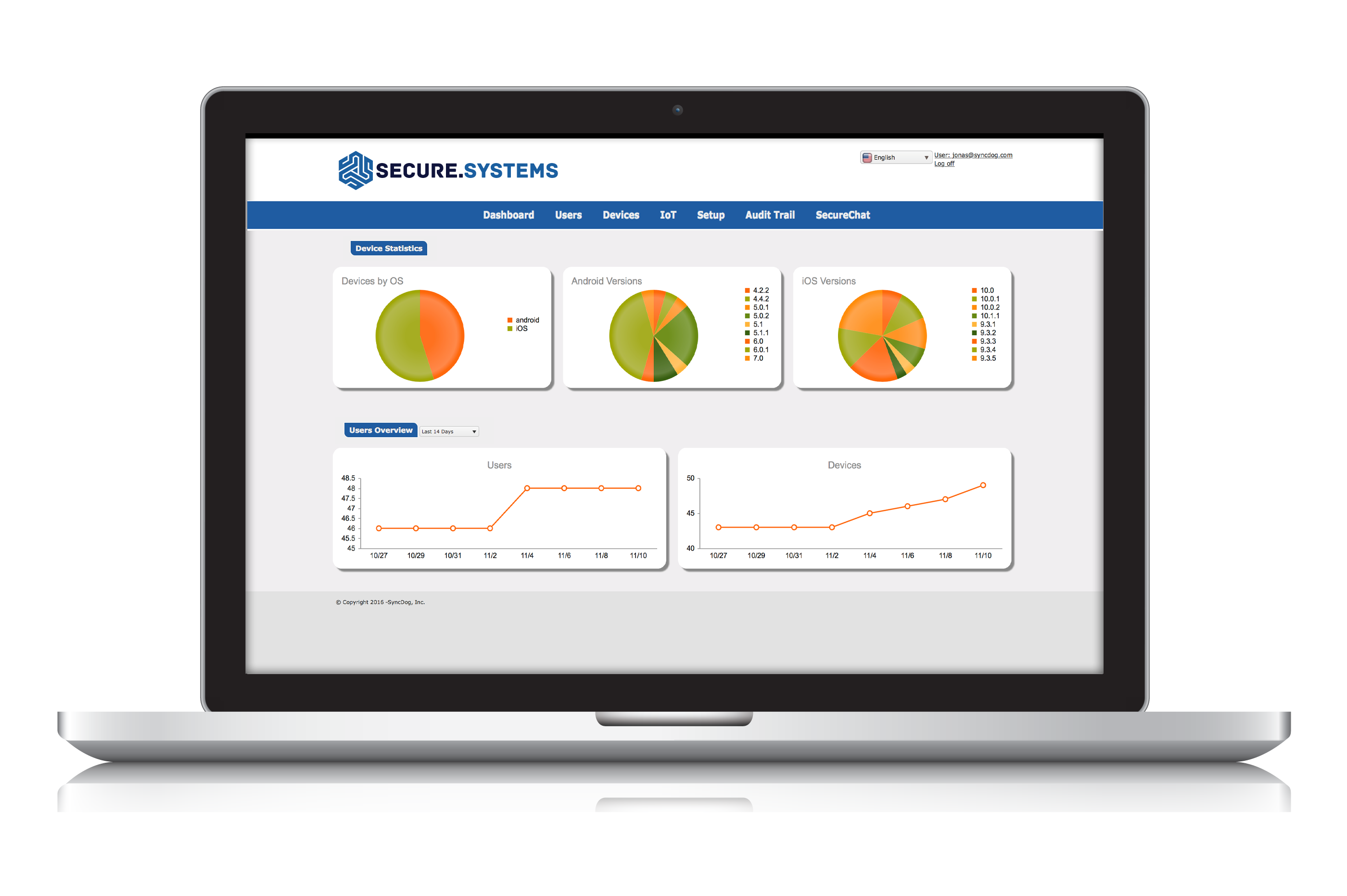
Simple, Easy Management
Administrators, employees and compliance managers all benefit from the easy management of Secure.Systems™. Privileged users can easily define the security rules within the app and also grant or deny corporate data access privileges on devices. If an employee leaves the company or a device is lost or stolen, corporate data inside the Secure.Systems™ container can be remotely erased without infringing upon the employee’s personal data.
“The speed and flexibility of the setup & configuration and at the right price point makes this an unbeatable solution.”
