Secure.Systems™, by SyncDog
The First:
Fully Integrated
End-to-End Mobile Security Solution

Tired of being chained to your desk?
You need SyncDog’s Secure.Systems™. Secure.Systems™ is a mobile security solution built with the mobile worker in mind. Watch to learn how to turn your personal device into a mobile office.
SyncDog, when your old EMM solution just isn’t enough!
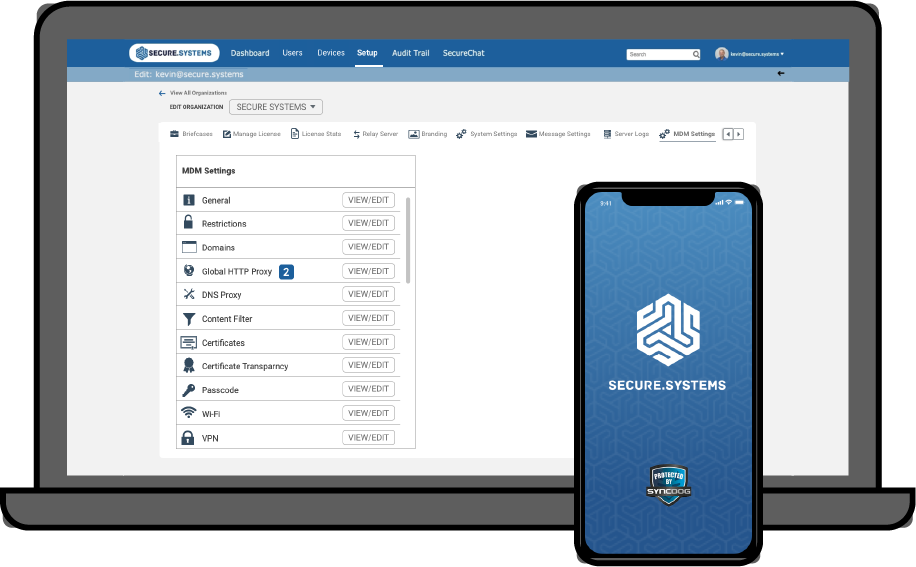
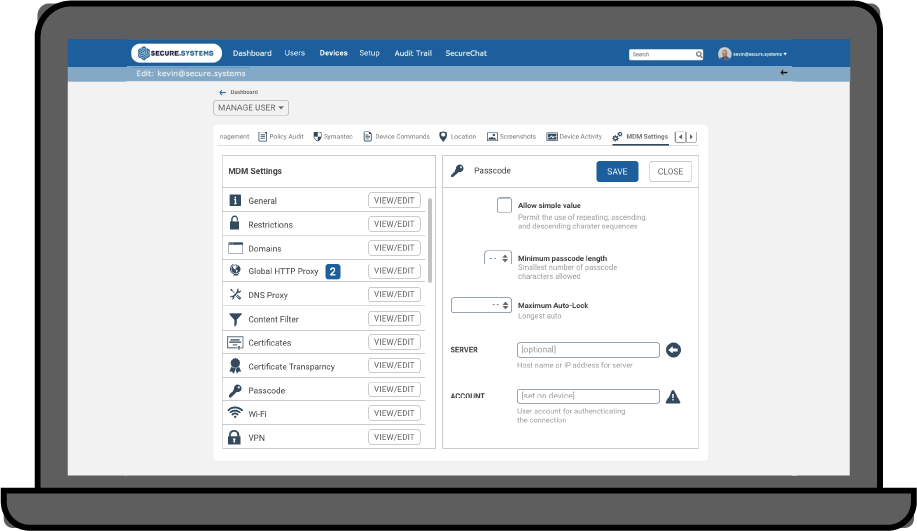
SyncDog provides one fully integrated modular solution that ensures…
Device Protection
Email & Data Encryption
Secure Support for BYOD
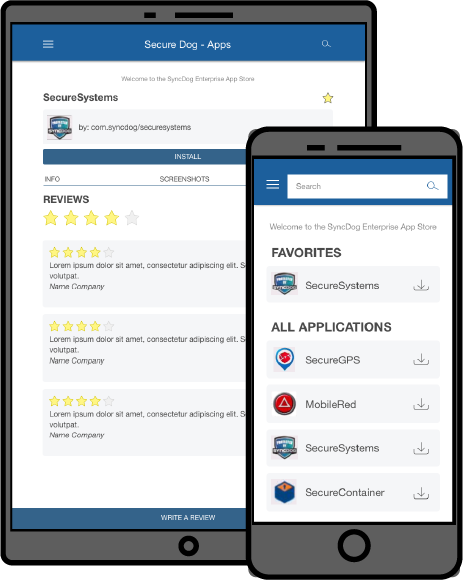
Native / Hybrid app store
Anti-Malware/Anti-Phishing
DLP / Dual Persona
IOS or Android
Role Based Functionality

Empower Your Mobile Workforce
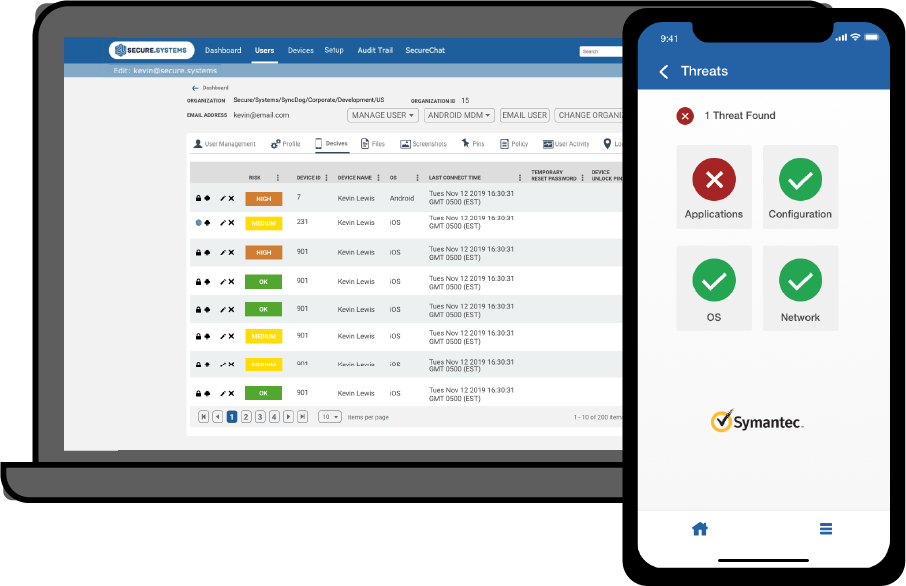
A single instance of our Secure.Systems™ solution can be utilized across your mobile workforce as well as 3rd party contractors and consultants.
Secure Unmanaged
BYOD
The Secure.Systems™ Workspace provides a secure application platform for employees accessing enterprise mobile productivity apps on BYOD or CYOD (Choose Your Own Device) devices.
Increased Productivity & Security
Our solution finally removes the technological struggle of having to choose between increased security or increased productivity. SyncDog enables you to have both.
See How Secure.Systems™ Can Secure Your Mobile Workforce
News
SyncDog Enhances Mobile Threat Defense Capabilities with Zimperium
On-Device Protection Detects Threats Targeting Mobile Devices in Real-Time RESTON, Va., July 22, 2020 -- SyncDog Inc., the leading Independent Software Vendor (ISV) for next generation mobile security and data loss prevention, today announced a partnership with...
SyncDog Partners with Ingram Micro to Expand Access To Secure.Systems
Inclusion in Ingram Micro's Cloud Marketplace Enhances Accessibility of SyncDog's Next Generation Trusted Mobile Workspace (TMW) RESTON, Va., July 1, 2020 -- SyncDog, Inc., the leading Independent Software Vendor (ISV) for next generation mobile security and data loss...
SyncDog Featured in The Silicon Review: 5 Best Cybersecurity Companies to Watch
The SyncDog team is pleased to share we have been listed as one of the 5 Best Cybersecurity Companies to Watch by The Silicon Review. Along with this announcement, our CRO Brian Egenrieder is featured in The Silicon Review's June 2020 Edition. Below is a...
Blog
Your Employees Don’t Want to Carry Two Phones, They Just Want Privacy
To BYOD or not BYOD? That’s the question many organizations are toying with. Bring Your Own Device (BYOD) policies are gaining traction amongst enterprises—primarily because of the cost-savings benefit—but there have been hesitations stemming from employees. If your...
The BYOD Dilemma in the Eyes of HR
To BYOD or not to BYOD, is there really any question any longer? According to market research, 85% of organizations implemented Bring Your Own Device (BYOD) policies during the COVID-19 pandemic. Even with BYOD becoming the de facto standard, companies and employees...
Your Zero Trust Strategy Shouldn’t Have an Asterisk Behind It *
* Does Not Apply if Device is Rooted or Jailbroken! A Zero Trust mobile architecture needs to protect in all scenarios – the MDM solution you are currently using will come up short. Many organizations and government agencies are looking to build out a Zero Trust...